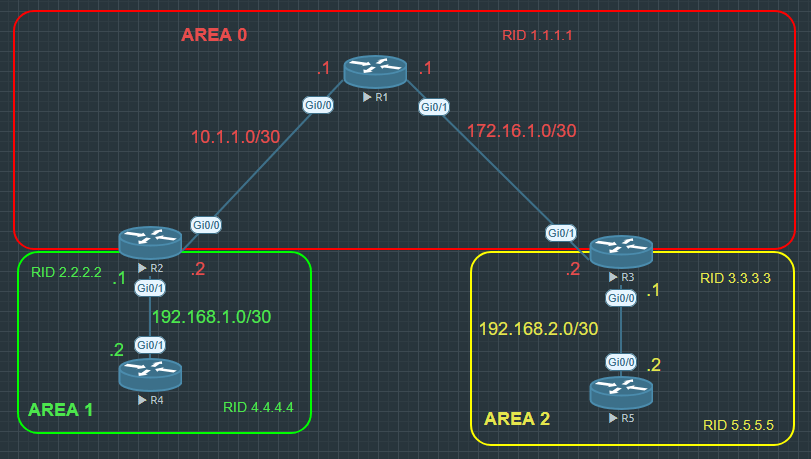
I’ve already done one post regarding EIGRP, but I said I was going to do a second post going over a few more advanced topics regarding EIGRP routing protocol. Check out my previous EIGRP post by clicking here.
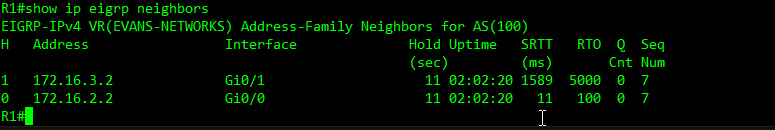
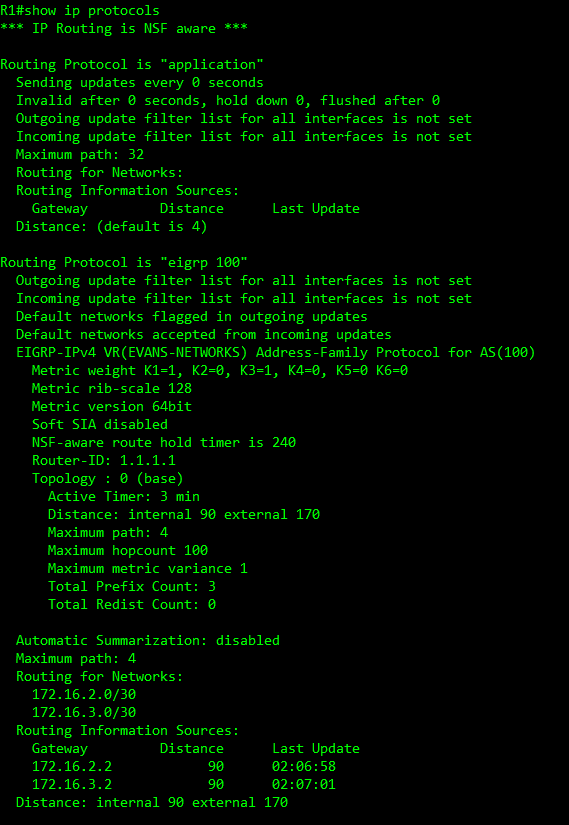
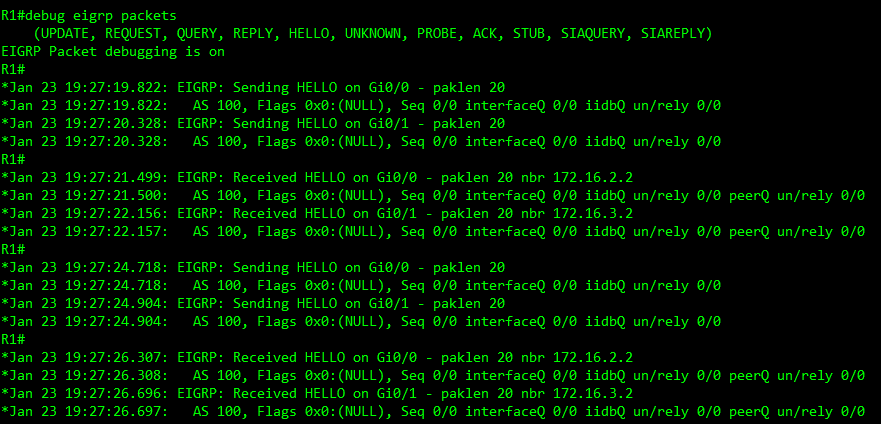
EIGRP uses Hello packets to check that their neighbors are still active, these packets are sent out default EIGRP hello timer is 5 seconds, slower interfaces it uses 60 seconds. EIGRP uses a told time to tell the neighbor how long to wait without receiving EGIRP packets back before it declares the neighbor down, by default 3 x hello packet are send, if the router receives EIGRP packets the timer is reset. If it fails to receive any EIGRP packets the neighbor is declared down for a Ethernet interface it would take 15 seconds (3x5s) to declare the neighbor is down or 180 seconds (3x60s) on a slower interface. You can adjust these timers per interface but applying the configuration on the interface itself with the following:
R1(config-if)#ip hello-interval eigrp 100 3 – 100 is the AS of EIGRP / EIGRP hello interval to 3 seconds.
R1(config-if)#ip hold-time eigrp 100 10 – 100 is the AS of the EIGRP / 10 is holding timer.
To verify these timers with the following command.
R1# show ip eigro interface detail gi0/1 | include Hello | hold
EIGRP Route Summarization is used to reduce the size of your routing table when you have a large number of routes you can summary them with EIGRP. This creates smaller routing tables, less routing updates, and improves stability. Older routers ISO have route summarization on by default, newer routers ISO have them turned off by default you can enable automatic summarization with the command auto-summary or no auto-summary, I would advise against replying on auto summary. Example of summarizing a route when you have the following networks:
10.0.0.0/24
10.0.1.0/24
10.0.2.0/24
10.0.3.0/24
Will summarize to 10.0.0.0/22
To find this you convert the last 3 octet into binary and see which match in this example converting the 3rd octet to binary to get the following
0000 0000
0000 0001
0000 0010
0000 0011
Common bits are 000 000
To find the subnet mask you calculate the following
1st octet (10): 8 bits
Second octet (0): 8 bits
Common bits in third octet: 6 bits
Subnet mask – 8+8+6 = 22
This will allow the following networks to be summarized 10.0.0.0 – 10.0.3.255
You would apply the route summary to the EIGRP interface
R1(config-if)# ip summary eigrp 100 10.0.0.0 255.255.252.0
EIGRP Stub routers limit their participation in EIGRP which benefits the networks making more efficient, scalable and stable. It works well in a hub and spoke design. EGIRP stub routers do not advertise routes learned from other routers. Stub Routers oonly advertises specific locally relevant routes. EIGRP Stub reduces EGIRP queries from flooding the network during route failures and prevents networks from slow convergence or stuck in active state as well as preventing routing loops.
EGIRP stube routers are configured with the following options, this chart is from a cisco router.
| Stub Type | Advertises |
| connected | Do advertise connected routes |
| leak-map | Allow dynamic prefixes based on the leak-map |
| receive-only | Set receive only neighbor |
| redistributed | Do advertise redistributed routes |
| static | Do advertise static routes |
| summary | Do advertise summary routes |
You can configure EGIRP stub routers with the following commands
R2(config)#router eigrp 100
R2(config-router)#eigrp stub connected | Summary | static.
EIGRP Authentication
EIGRP Authentication is configured to ensure that only authorized routers are able to form neighbor adjacency. EIGRP password is included in the EIGRP packets, and the neighbor router decrypts the hash, if the password does not match the packets are discard and a neighbor adjacency does not form. EIGRP encrypts the password by using MD5 authentication and the keychain function. Keychain is used for authentication between devices, it’s like a name list for shared secret keys that are used for routing protocols to verify routing updates. You would configure EIGRP Authentication with the following commands:
R2#config t
R2(config)#key chain KEYCHAINNAME
R2(config-keychain)# key 2
R2(config-keychain-key)# Key-string PASSWORD
R2(config-keychain-key)#int gi0/0
R2(config-if)#ip authentication mode eigrp 100 md5
R2(config-if)#ip authentication key-chain eigrp 100 KEYCHAINNAME
If you’re using named EIGRP you would do the following commands
R1#config t
R1(config)#key chain KEYCHAINNAME
R1(config-keychain)# key 2
R1(config-keychain-key)# Key-string PASSWORD
R1(config)#Router eigrp EVANS-NETWORKS
R1(config-router)#address-family ipv4 unicast autonmous-system 100
R1(config-router-af)#af interface default
R1(config-router-af-interface)#authentication mode md5
R1(config-router-af-interface)#authentication key-chain KEYCHAINNAME
You should see the neighbour adjacency come up if configured correctly.
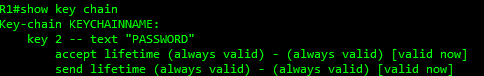
to troubleshoot your keychain, you can do the following commands
R1#show key chain
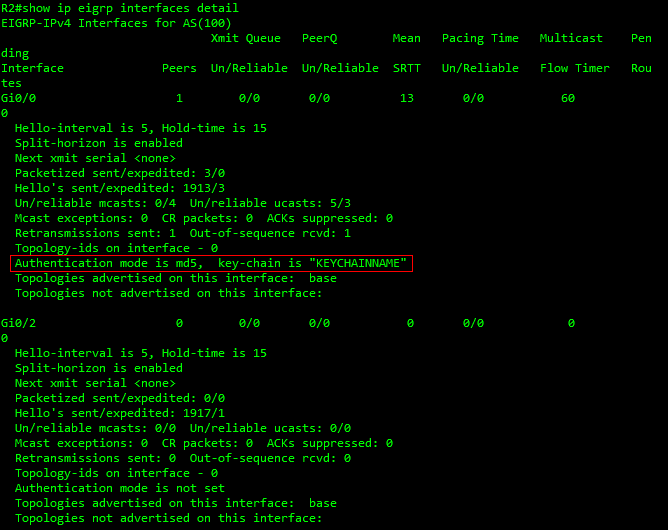
R2#show ip eigrp interface details
That’s the end of my post for EIGRP more advanced topics, let me know if you have any questions or would like me to cover something else. I do have plans in the future to do a post with route redistribution with EIGRP and OSPF. Make sure you check out my other EIGRP post here.